RITSEC CTF
Hosted with <3 by RITSEC, a student-run club at RIT
#RITSEC
November 17 - November 18 2018
RITSEC 2018
This was my second CTF, and I found it much more challenging than the Bank of America-sponsored CTF that ran at DerbyCon 2018. This was also where I started taking notes about my process, but was doing so on paper. At the time of writing, the CTF site was still accessible, but the related web servers were not running, so some of the flags are not reproduced here.
Burn the candle on both ends (Forensics)
It's a two step problem
The challenge included a JPG file (of a cute dog wearing a stegosaurus costume!).

I began by opening the file in a hex editor and searched for the standard FFD9 end to the JPG file. Following those bytes, there was the start of a ZIP file (PK). I cut the JPG portion away and resaved as file.zip. The formatting was good, and the file requested a password to unzip. After searching fruitlessly through the contents of the ZIP and JPG files, I took a guess based on the image, and the password was “stegosaurus”.
RITSEC{8U51N355-1N-7H3-Fr0N7-P4r7Y-1N-7H3-84CK}
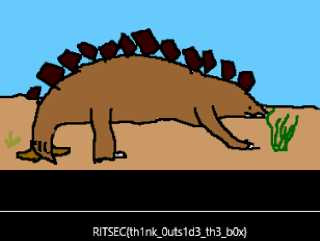
I am a Stegosaurus (Forensics)
Look Closely
That clue and the included stegosaurus.png file included were not much to go on, so I started looking at the file in a hex editor. A bit of Googling later, and I had the start and end bytes of a PNG files, but this file did have the normal start and end bytes in place.
I tried running it through an online steganography tool (osric.com/chris/steganography/decode.html), but no hidden image was found.
I tried a binwalk of the file, but it only turned up the header and IDAT sections.
Finally, I ran it through pngcheck and got my first interesting result – a CRC error in the IHDR corrupted as 01aae416 expected 93cf1eca – so the CRC check was bad on the file. I copied the expected CRC into the stegosaurus.png file in place of the 01aae416, and the image rendered correctly:
The Tangled Web (Web)
fun.ritsec.club:8007
The provided link led to a website with a series of links from words and short phrases that soon became obviously song lyrics. After running through some of the paths without finding any clear solution, I ran a site map (www.xml-sitemaps.com). In the results I did come across a page Fl4gggg1337.html, but it turned out to be red herring. Going through the remaining pages, and looking at the pages in the web Inspector, I found the page Stars.html, which contained an HTML comment “Remove This Note Later” (which I think is for use in the Lazy Dev challenge that I didn’t get to) and a hidden line of characters ending with the = padding of a Base64 string. Running the string through a Base64 decoder provided the flag.
Space Force (Web)
The Space Force has created a portal for the public to learn about and be in awe of our most elite Space Force Fighters. Check it out at fun.ritsec.club:8005!
The link in the clue led to a website with (as I recall it) a text field and submit button and some areas that display information retrieved about some space ships. I think there were several ship names suggested. I tried the obvious “flag”, but that got me nothing. I captured the HTTP requests in Burp Suite and could see the variable “name” referenced, but didn’t know what to do with it.
I hadn’t learned much basic web hacking, yet, so this one beat me. I was pretty sure it required SQL injection, and I did try several variations on ‘or1=1, but with no success. I did, however, get “Something went wrong with your query! What are you trying to do?” out of it. In retrospect a bit more perseverance would likely have dumped the contents of the space ship database.
Lost in Transmission (Crypto)
Attention to detail is key
Add curly braces and underscores to the flag ;) Also CAPSLOCK on ritsec
The challenge included a Lost_In_Translation.txt file with the following text:
MTAxMTAxMDEwMTExMDEwMTAwMTAxMDEwMTExMTAxMDEwMTEwMTAxMDAxMDExMDEwMTAwMTExMTAxMDEwMTE
xMDAxMDEwMTAxMTEwMDEwMTAxMDEwMDExMDEwMTAwMDAwMDAxMDEwMTAwMTExMTAxMDEwMDAwMDAxMDEwMTA
wMDAwMDEwMTAxMDEwMDExMDEwMTAwMDAwMDAxMDEwMTAwMTExMTAxMDEwMDAwMDAxMDEwMTAwMDAwMDEwMTA
xMDEwMDExMDEwMTAwMDAwMDAxMDEwMTAwMTExMTAxMDEwMTExMDAxMDEwMTAxMTEwMDEwMTAxMDEwMDExMDEwMTA=
The = padding indicated a Base64 encoded string, and decoding it resulted in a binary string. I checked that decoded as binary and got a hex string, but got no further. The = may be a red herring, and there’s more going on with the repeated elements.
Bucket ‘o Cash (Forensics)
https://s3.amazonaws.com/ritsec-ctf-files/memorydump
CentOS 7.5 [hint added later]
This was a memory dump file, and a cursory examination showed a Linux file and folder structure (e.g. /tmp/tmux-o/def), and I narrowed it down to a CentOS 7 distro before the hint went up. I tried running Volatility in Kali (volatility imageinfo –f ~/Downloads/memorydump), but couldn’t seem to get a working Volatility profile for this OS.
FINAL RESULTS
Final Score: 611/7586
Final Rank: 350 out of 952