BSidesTO 2019 HackFest CTF
The competition, meant to be accessible to all, will be running in a relaxed and social atmosphere. You will encounter different type of tracks such as: Vulnerable bitstream, Krasnikov, Beginner track, Offline SDR and more. Join us for a Hackfest flavoured CTF!
@BSidesTO @hackfest_ca
October 6 2019
BSidesTO 2019 HackFest CTF
This is my somewhat disjointed recollection of the challenges we tackled in the BSidesTO CTF. The highlight of the challenge set was definitely the software-defined radio challenges – not something we see often in CTFs. Unfortunately, working with a partner and working fast, I didn’t take the kind of clean notes that usually make it easy to write these up. That speed and collaboration, however, did bring us a win. Here is the best of my recollection in no particular order.
Exfiltration (Pcapng)
We need you! We need that you find what kind of data we lost :( Good Luck!
We are provided with the RussianCupid.pcapng file.
I opened the capture in Wireshark, and right away checked the Export Objects list. There, I noticed the Just4You image file and saved it. Opening the file reveals the flag in the saved image.
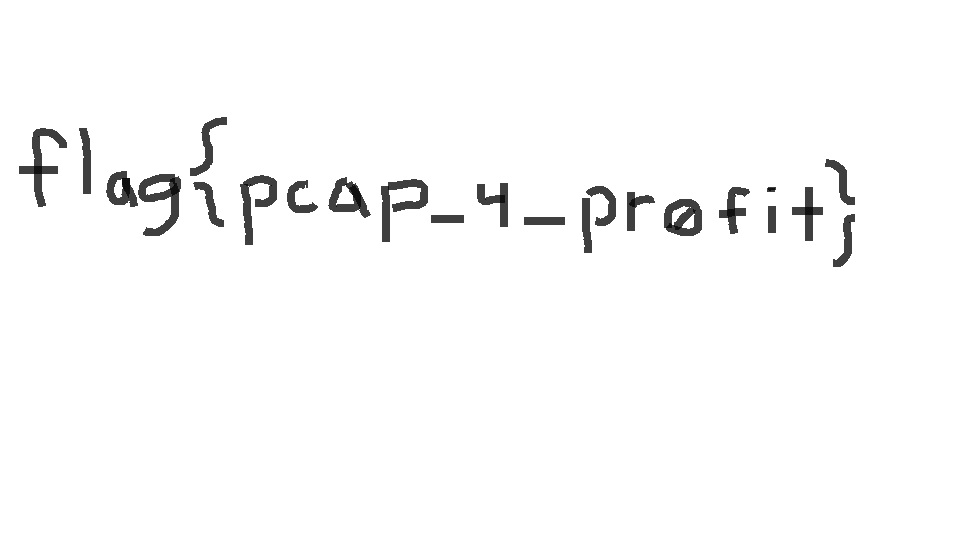
Base64 (Beginner Cipher)
If you see a string that seems encoded, contains only numbers, letters, / and = and might finish with either one or two = (but not all the time) you should try this decoding method. It is also used by pentesters to transfer files over the network and to make sure we are not missing any parts.
Here is the string : SEYtNmQzZTdmMTlhNjhlM2FjOWY4ZGM2ODNhYTJlNjFlZDY=
This was very clearly a Base64-encoded string, and it decodes to the flag:
HF-6d3e7f19a68e3ac9f8dc683aa2e61ed6
Julius (Beginner Cipher)
One of the first used cipher in history.
Challenge:
XV-vvrru3u1627s71rvru5suut8sus9s6q9
Again, clearly a Caesar cipher and a simple decode to the flag:
HF-ffbbe3e1627c71bfbe5ceed8cec9c6a9
Crawler (Beginner Web)
What page does a crawler check to see where he can and cannot go? Use the server beginner-web.hfctf.org. The answer is a full flag not just the file name.
Another perennial favourite…what’s in the robots.txt file? The flag:
HF-DA371569A494D6953447F68C2F6316B2
Port Scan (Beginner Web)
By default, nmap will only scan the top 1000 ports. Can you learn how to fix this? If you find a weird port, you can poke it with nc (netcat).
Address: beginner-web.hfctf.org
Recommended Tools: nmap, nc (netcat)
A simple port scan using nmap (nmap beginner-web.hfctf.org -p1-65535) shows us only one port over 1000 was active and that was 8080 (http-proxy). I don’t seem to have the flag in my notes, but poking it with netcat (nc beginner-web.hfctf.org 8080) was the way to go.
Look around… (SDR)
Head to https://sdr.hfctf.org/
Look around this webpage. Can-you find anything revolving around the "CDN" it uses?
Flag is case-sensitive
Looking around at the site code, my partner saw that the banner image was located at sdr-cdn.hfctf.org. Opening the image in a new tab, he came across the flag in the full URL, which was for an S3 bucket with an interesting folder name:
https://s3.us-east-1.amazonaws.com/flag-qg7y1k1cjjozpov03uwn/images/pic02.jpg
flag-qg7y1k1cjjozpov03uwn
A voice from beyond (SDR)
The files are in RAW IQ format; They have been recorded at a sample rate of 1800000 samples per second, at the frequency set to 433Mhz.
Opening up the provided flag1.raw file in GQRX, and tuning to the frequency range provided in the hint site at sdr.hfctf.org, I was able to tune in to a clear signal. With a bit of fiddling with the options, I settled on WMFM(mono) and could hear a voice reading out phonetic alphabet letters (foxtrot.lima.alpha…). Put them together and you’ve got a flag:
flag-sdrrocksf
Other SDR Challenges (SDR)
I don’t recall which challenge was which of the 4 remaining, but there were two more SDR RAW IQ files (flag 23.raw and flag4.raw). Flag23.raw included a signal that was clearly Morse code. I was able to take a .WAV recording of the signal, which I could upload to SC Phillips’ Morse Code Decoder (https://morsecode.scphillips.com/labs/decoder/), which decoded the Morse code to:
FLAG-MORSEOVERSDR
I’m not sure if we got another of the SDR challenges solved, but flag4.raw contained what appeared to be a pager signal, but I couldn’t get the multimonNG decoder to output anything before time ran out on us.
LazyTiger (Privacy)
I don’t recall the clue, but we were provided with the LazyTiger.jpg file

Opening it in HexFiend, we can see that it is a properly formed JPG file, with no embedded ZIP files. The header includes an EXIF tag, so Jeffrey’s Image Metadata Viewer (http://exif.regex.info/exif.cgi) was the next logical stop. There, we could see that the Camera was listed as TigerBrand SuperPro and the Lens model was listed as CTF. Looking closer, both the Camera and Lens serial numbers were the same and, by adding an “HF-“ fit with the flag format seen in many of the challenges:
HF-666C61677B6173747574655F74696765727D
Encrypted (Beginner Steganography)
This simple file contains 3 flags. Can you dig deep enough?
A binary series was included in the clue, but I don’t have a record of it, as was FILE.zip.gpg. The GPG file requires a passphrase to open it, and the binary series (decoded to ASCII) was the key. Once opened, we had FILE.zip, which opened to the folder FILE, containing FILE.jpg (the string base64-decodes to: “well-Plard”) and FLAG.txt with the text:
The Missing Parts (Broken Stream)
I don’t have the clue or the stream site, but there was a video stream that was showing a series of contantly changing letters and numbers and highlighting one at a time. Taking the highlighted ones when they popped up we had the beginning of a flag but were missing about 4 characters in the middle of the string. During the highlighting of this section of the string, the colours inverted. My partner worked more on this, trying to recover the missing stream components and playing them one at a time – I seem to recall some website file enumeration was involved to locate the “missing” stream elements. Once he located the 2 second elements that were missing, it was just a matter of playing them back and noting the highlighted characters to build the complete flag:
FLAG-5V3Q4UK4DatW
Déjà vu (Broken Stream)
This was based on the same stream as “The Missing Parts”, but relied on finding an entire “inverted” stream, which was the rest of the section that we saw inverted colours for while building the first flag. Again, with the stream elements located, it was just a matter of playing them and recording the complete flag:
FLAG-fptKwfUxh6vp
Movie (Beginner Trivia)
What movie is this quote from?
Quote: Hack the Planet!
Hackers, of course.
Ports (Beginner Trivia)
How many TCP ports can be open at the same time?
65535
FINAL RESULTS
Team :
Final Score: 1314
Final Rank: 1
The Club's First First-Place Finish!
Me :
Final Score: 972
Final Rank: 4