NeverLAN CTF
Middle School Focused Capture The Flag Event
#TeachThemToHack
January 31 - February 3 2019
NeverLAN 2019
This was a lot of fun. We used this as the introduction to CTFs for our new Cybersecurity Club, and it delivered a nice range of difficulty levels - enough to keep everyone engaged and learning. We started in the club meeting on the evening of the event's first day and by the end of the hour most groups had a solution to one challenge or another. I mostly worked on it over the weekend (last two days), and I know I learned a thing or two, and even had a chance to go back over some that my teammates had solved already to see if I was on the right path.
As this CTF and write-up may appeal more to beginners, I've included more detail (specific Linux commands, etc) here. Challenges are listed in the roughly the order I started them, rather than in groups by challenge category (Web, Crypto, etc)
WebCipher (Scripting/Coding)
To verify that only computers can access the website, you must reverse the Caesar cipher There are a list of possible words that the cipher may be here https://challenges.neverlanctf.com:1160
Just the word “Jllnunajcxa” and a text field with a submit button.
In spite of the category, no actual coding was used here – I just copied the cipher text into the Caesarian shift cipher encoder at http://rumkin.com/tools/cipher/ and cycled through the letter shift option until an English word was produced. The deciphered text was “accelerator” and when submitted to the form, the flag is revealed: flag{H3llo_c4es3r}
Unexpected Intruder (Recon)
occurring in Chicago, Illinois, United States, on the evening of November 22. There was an interruption like nothing we had ever seen before.
What was the name of the Intruder?
Really just a trivia challenge, but a quick Google search shows that the infamous Max Headroom pirate TV broadcast was on November 22 on a Chicago station. The real trick was just figuring out the flag format: flag{MaxHeadroom}
Purvesta (Recon)
I love Github. Use it all the time! Just wish they could host a webpage...
This was super obvious to me, as I have just been putting together my own github page, so a quick browse over to purvesta.github.io brought me to purvesta’s homepage. It mentions work on CTF and a link to their github repo lol where the flag is located: flag{This_github_l00ks_a_l1l_sparc3}
Filling a need (Recon)
This organizations creation was announced Mon Sep 24 2001
What is the full name of the organization?
Again, really just a trivia question. Some quick Googling reveals that OWASP was announced on 24 Sept 2001. And again, the trick was formatting the flag: flag{OpenWebApplicationSecurityProject}
Binary 1 (Binary)
A user accidentally installed malware on their computer and now the user database is unavailable. Can you recover the data and the flag?
Flag is All Caps
A users_db.dms file is included. A quick examination of the file with a hex editor shows lines and lines of hex. I copy pasted that hex into Burp Suite’s Decoder. The result of decoding as Ascii hex was lines and lines of what looked like Base64. Decoding that as Base64 gave some garbled plain text that was clearly database fields and entries. By deleting the returns and bringing it into one line, the garbling went away. Now, this was over 1800 lines of material, so I copied the garbled text into Word and did a quick search for “flag”, which did turn up an entry but most of the flag was garbled. I copied the same garbled text into BBedit, which has clear line numbers and found the lines containing the garbled flag. I then copied the Base64 lines into BBedit, found the same lines, and copied a dozen or so of them back into Burp Suite. A dozen lines is much easier to format to one line than 1800, and once that was done, I decoded as Base64. This came out really garbled, but after deleting a couple of the leading characters of the Base64, the decode resolved to plain text with the flag:
flag{ ENC0D1NG_D4TA_1S_N0T_ENCRY7I0N}
Binary 2 (Binary)
Our lead Software Engineer recently left and deleted all the source code and changed the login information for our employee payroll application. Without the login information none of our employees will be paid. Can you help us by finding the login information?
***Flag is all caps
An Employee_Payroll.exe file is included. Again, a quick examination with the hex editor showed some interesting characters right near the top:
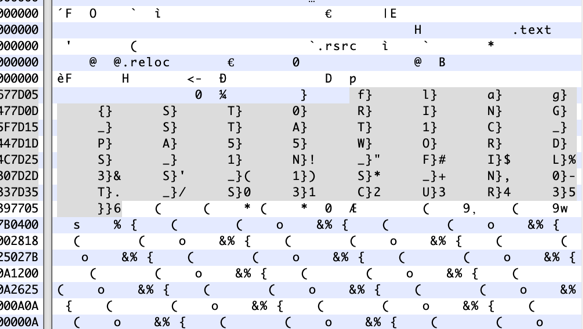
Taking the characters before each }, we get the flag: flag{ST0RING_STAT1C_PA55WORDS_1N_FIL3S_1S_N0T_S3CUR3}
Cover the BASEs (Crypto)
ZmxhZ3tEMWRfeTB1X2QwX3RoM19QcjNfQ1RGfQ==
Between the clue and the == padding at the end of the string, this was pretty clearly a Base64 encoded string. Using the decoder at base64decode.org, the result is the flag: flag{D1d_y0u_d0_th3_Pr3_CTF}
Oink Oink (Crypto)
This included an oink_oink_challenge.png file:

Between the formatting (numbers and {} as clear text), and some experience with the different ciphers at http://rumkin.com/tools/cipher/, I recognised it was one of the Substitution ciphers (in this case PigPen ##XX). Running it through that decoder, the flag is: FLAG{D0WN_AND_D1R7Y}
Alphabet Soup (Crypto)
This is all that’s included here:
MKXU IDKMI DM BDASKMI NLU XCPJNDICFQ! K VDMGUC KW PDT GKG NLKB HP LFMG DC TBUG PDTC CUBDTCXUB. K'Q BTCU MDV PDT VFMN F WAFI BD LUCU KN KB WAFI GDKMINLKBHPLFMGKBQDCUWTMNLFMFMDMAKMUNDDA
Now, the punctuation, the K’Q, KN, KB, and K got me started with a simple letter substitution cipher. I just copied the whole thing into Word and started using Replace All for the letters that looked like they were forming words, starting with K for I and Q for M. I replaced the uppercase letters with lowercase letters to clearly see which ones I had replaced and which I hadn’t. This appears to be the intended method, since the flag is: flag{doingthisbyhandismorefunthananonlinetool}
Super Old School (Crypto)
The image is trying to tell you something.
This included the SuperOldSchool.png file:
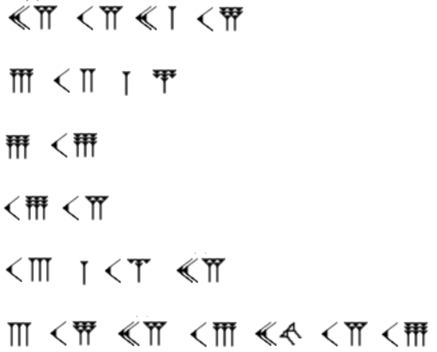
There are some benefits to a classical education, and I recognised the cuneiform figures immediately. A quick Google showed that these are cuneiform numerals – the C-shapes are 10s and the groups of triangles on sticks are groups of 1s, and the two on their side are a 0:
25 15 21 18
6 12 1 7
9 19
19 15
13 1 14 25
3 18 25 16 20 15 19
The for number grouping 6 12 1 7, looked like the number places of the letters F L A G, and the rest decode to: YOUR FLAG IS SO MANY CRYPTOS
Now, we get to test the formatting and the typo and end up with: flag{YOURFLAGISSOMANYCRYPTOS}
Cookie Monster (Web)
It's a classic https://challenges.neverlanctf.com:1110
Browsing to the provided URL brings up a simple page that just says “He’s my favorite Red guy”. Using the web Inspector, it’s possible to view the cookies for the page (Storage tab in Safari), which shows a cookie with the fields Name: Red_Guy’s_name and Value: NameGoesHere. Now, I was initially stymied on this one, because Safari wouldn’t let me edit the cookie here. Once I opened it in Chrome, it was smooth sailing. In Chrome, the cookies are found in the Application tab (Storage section). There I changed the Value to “Elmo” and refreshed the page to get the flag: flag{YummyC00k13s}
Things are not always what they seem (Web)
if you can't find it you're not looking hard enough
https://challenges.neverlanctf.com:1165/hello.html
Browsing to the URL provided, there is a Rick Astley gif and a little text. Using the web Inspector, the following was coded as white text on the white background:
Well, look at you go! You can see that sometimes everything isn't as it appears... flag{Whale_w0u1d_y0u_l00k3y_th3r3}
SQL Fun 1 (Web)
REPORT: 'My Customer forgot his Password. His Fname is Jimmy. Can you get his password for me? It should be in the users table'
https://challenges.neverlanctf.com:1150
The provided URL leads to a page with the clue and a text field and submit button. Quite clearly, this requires a SQL query (it’s a bit much to call it an injection). The correct formatting for this query is:
SELECT Password FROM users WHERE Fname=’Jimmy’
Submitting this returns the flag: flag{SQL_F0r_Th3_W1n}
SQL Fun 2 (Web)
REPORT: A Client forgot his Password... again. Could you get it for me? He has a users account and his Lname is Miller if that helps at all. Oh! and Ken was saying something about a new table called passwd; said it was better to separate things
https://challenges.neverlanctf.com:1155
Again, we are presented with a page with the clue and a text field and submit button. This will clearly take multiple queries, so the correct formatting for the first is:
SELECT * FROM users WHERE Lname=’Miller’
This returns:
id 5
Username DisUser
Fname Tom
Lname Miller
Email Miller@example.com
There is an additional clue here: maybe try JOINing another table
So, now we have some information to query the other table, including id and Username fields that are likely keys in the other table. I dispensed with the JOIN and made my second query:
SELECT * FROM passwd WHERE id=5
Unfortunately, this gave a nonsense password, but it did give me another field:
id 5
user_id 4
Password Tm9wZS4uLiBXcm9uZyB1c2Vy
So, I reformatted the query to:
SELECT * FROM passwd WHERE user_id=5
This returned a Password entry padded with =. Decoded at base64decode.org, the flag is: flag{W1ll_Y0u_J01N_M3?}
Return of the Sith – Part 1 (Forensics)
We've been given a specific forensics case by a really grumpy customer. He starting smashing consoles and stuff when he found out what happened (video).
Looks like he was hacked. Here's the VM Download you'll use:
https://files.utahcon.org/file/neverlan/NeverLAN%20CTF%2064-bit%2018.04.1.7z
7z md5 hash: cfb95b3d837602f1932fa309aafd8aff
Password to uncompress: the_path_to_the_dark_side
User's Password:ikilledmydad
Challenge:
After a quick gander, we realized the user installed VNC with a crappy password. Can you get the password he used so we can prove to him it was bad?
Note: The password is the flag, it is not in the flag{} format
Downloading and logging in to the VM, it’s an Imperial Star Wars-themed Ubuntu machine owned by Kylo Ren. In the terminal I ran ‘top’ and saw the xtightvnc process pop up from time to time. A bit of Googling on xtightvnc revealed that it keeps its password in the file passwd found in the ~/.vnc folder. Sure enough, the passwd file was there, but the password was encrypted.
Since I was working with an OVA appliance file that I could just reload if I changed anything important for subsequent challenges, I installed git (sudo apt install git) and make (sudo apt install make), the latter of which required an update to the OS (sudo apt-get update). This let me clone a git repository for a VNC password decrypter (git clone https://github.com/jeroennijhof/vncpwd.git) and install it (make). I ran vncpwd on the passwd file (./vncpwd ../passwd) and got the password/flag: darthvad
Return of the Sith – Part 2
We've been given a specific forensics case by a really grumpy customer. He starting smashing consoles and stuff when he found out what happened (video).
Looks like he was hacked. Use the VM provided in Part 1.
Challenge:
Since they got in with VNC, they were locked into his user account, without any root access.The user used SUDO for 'protection' so that means he’s safe from the attacker getting his password, right? The goal here is to figure out if the user was able to escalate to root without having the user's password. DO BE CAREFUL since messing with a VM has the ability to remove traces of what you’re looking for. This IS a forensics challenge.
I used the original appliance to reload the VM, so that the logs would be intact and unaltered by my previous search. Changes to passwords should be found in the authorisations log, so that’s where I started (cat /var/log/auth.log).
There’s lots of activity for Jan 29 and 30, most of which looks like just the setup of the VM with updates, curl, Rhythmbox, freedesktop, tightVNCserver, etc.
At 1913h on Jan 30, a new user is added (“mysql” with the home directory of “/root/”). This will presumably allow the user mysql to access the root directory, which we currently cannot do. The user id is changed from 1001 to 599, and the user is added to the newly created mysql group and to the sudo group.
There is a hashed password in the /etc/shadow file for mysql.
$6$Pvd5Xu81$4TTcZUBR2mWv4a8zS.MQYjbtyeWwpQRSqcVK.6l8.8TTAZMCtrsIeSgUaCg0chDhJtrflmohgaVnH9afZTcQN0
The $6$ at the beginning of the hash indicates SHA-512 is the hashing algorithm, confirmed by looking at the ENCRYPT_METHOD in the /etc/login.defs file. That is followed by the salt Pvd5Xu81, and the hashed password 4TTcZUBR2mWv4a8zS.MQYjbtyeWwpQRSqcVK.6l8.8TTAZMCtrsIeSgUaCg0chDhJtrflmohgaVnH9afZTcQN0
In order to crack the hash, I copied the /etc/passwd and /etc/shadow files to my Kali VM as passwd.txt and shadow.txt and merged them using unshadow (unshadow passwd.txt shadow.txt > passwords.txt). I edited the passwords.txt to only include the mysql entry (to reduce processing time) and ran the result through John the Ripper:
John –wordlist=/usr/share/wordlists/rockyou.txt passwords.txt
The SHA-512 salted hash format was recognised right away, but the cracking takes quite a while…and came up with nothing. In retrospect, that’s not surprising, since it’s likely a long passphrase for the flag.
As an aside, I came across another way to gain root access using sudo. First, create a hash of a password like ‘testpass’ (openssl passwd testpass), and copy the result into the second position of the root entry in /etc/passwd (sudo vi /etc/passwd). This overrides the hashed password in /etc/shadow, and you can switch users to root (su root and use password: testpass).
Return of the Sith – Part 3 (Forensics)
We've been given a specific forensics case by a really grumpy customer. He starting smashing consoles and stuff when he found out what happened (video).
Looks like he was hacked. Use the VM provided in Part 1.
Challenge:
Ok, great. They had full root access, did they leave anything else behind? Any other backdoor?
Notes: This one is also not in the flag format, but the flag will be the 'identifer' of the back door. If you think you've found it, but it's not accepting your challenge, you can message bashNinja on the NeverLAN Slack and he will verify if you've gotten it correct or not.
While John was quietly cracking the hash from Part 2, I moved on to Part 3.
In the auth.log, I noticed that ssh was installed after the mysql user was added and several connections were made to mysql from 192.168.0.13 (ports 37808 and 37814) over SSH. The VM is set to a bridged virtual NIC, so I added an internal network NIC and tried to connect (as root, since I was still waiting for the mysql password hash to crack)
After installing net-tools (apt install net-tools), I was able to use ifconfig to get the IP of this VM (192.168.2.44), so I could connect to it from the other.
In the Cloud (Cloud)
http://neverlanctf.cloud/
Welcome to the Cloud Level 1 challenge!
Through these various levels you'll discover common mistakes and problems when using Amazon Web Services (AWS), Google Cloud Platform (GCP), and others. There are no SQL injections, XSS bugs, buffer overflows, or vulnerable service to be exploit. Just raw cloud. What's included:
All challenges are inclusive of sub-domains of NeverLANCTF.cloud.
Level 1
This level is *buckets* of fun. See if you can find the first sub-domain.
Now, I started by using Knock to enumerate all of the neverlanctf.cloud subdomains, and immediately got level2:
level2-e8a0ed21fc6fcc73b90895b4a2cdb120dca.neverlanctf.cloud
and
neverlanctf.cloud.s3-website-us-west-2.amazonaws.com
but the latter just took me back to the Level 1 page and chastises me about shortcutting.
A little Googling on bucket names showed me an example bucket and I followed the pattern: bucketname.s3.amazonaws.com to get neverlanctf.cloud.s3.amazonaws.com.
That bucket contains an XML file with a Contents Key field:
flag-e8ff76090aefae7a958175254ccae055ed0ab6c3.html
at:
http://s3.amazonaws.com/doc/2006-03-01/
Combining them, we get:
http://s3.amazonaws.com/doc/2006-03-01/flag-e8ff76090aefae7a958175254ccae055ed0ab6c3.html
Where we find an unstyled XML file with Code: AccessDenied
And HostID: pqvlCG47wBUUqdgSAn4W09/j7YV0a+FTM7QtyWzAPrEFJT4HEnzM5DBftsw3mBO8yDewnctdRf8=
The = padding indicates Base64 encoding, but the decoded result is not readable
Going back to the first bucket, there is also a Contents Key field: index.html
It gives a similar result.
So, after a bit more Googling on the format of AWS buckets, I found that the format should be bucketname.s3.amazonaws.com/key
Sure enough,
neverlanctf.cloud.s3.amazonaws.com/flag-e8ff76090aefae7a958175254ccae055ed0ab6c3.html
gets us to a page with the link to level 2 and the flag:
http://level2-e8a0ed21fc6fcc73b90895b4a2cdb120dca.neverlanctf.cloud/
flag{ItsNotAsEasyAsItUsedToBeToHaveAPublicBucket}
In the Cloud 2 (Cloud)
http://level2-e8a0ed21fc6fcc73b90895b4a2cdb120dca.neverlanctf.cloud/
Welcome to the Cloud Level 2 challenge!
This level is quite similar, but might be a bit more challenging, but only because you need to have an account. You just need the free tier. See this HTML for a hint.
Level 2
This level is *buckets* of fun. See if you can find the flag and the next sub-domain.
So, we’re looking for multiple buckets, I guess, and a quick look in the web Inspector shows an additional commented note:
<!-- ask for a hint in the gameboard puzzle if you really can't create a free account. Having a free account really will help you later as you learn to hack -->
I started with another Knockpy search for subdomains for this URL, but came up with nothing
February 14th(Crypto)
3,9,13,15,18,7,20,1,4,14,5,21,6,2,17,10,8,16,12,11,19
Please input the flag with no spaces! :)
This includes a February_14th.txt file:
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| J | O | W | W | A | S | Q | L | L | W | E | I | U | S | B | A | E | S | I | P | L |
| O | W | W | A | Q | A | P | K | E | Q | I | O | O | Q | D | Z | R | D | O | U | E |
| E | D | E | F | B | W | I | J | M | I | K | M | L | W | E | C | Y | E | I | R | O |
| D | Z | S | D | M | P | W | H | L | A | L | K | M | E | L | K | U | W | Q | T | W |
| L | D | D | L | V | I | D | W | O | S | G | I | N | Z | U | K | K | I | Z | G | D |
| Z | M | H | M | D | W | A | Q | Y | L | I | S | B | V | E | P | M | P | B | Q | Z |
| E | B | G | I | J | Q | S | A | T | M | S | W | J | C | W | L | V | Q | H | M | S |
| G | N | U | O | O | D | F | Z | D | B | A | T | K | N | R | U | D | K | I | P | L |
| S | P | I | L | R | F | Q | B | H | H | B | U | O | Q | T | U | I | L | F | U | K |
| W | I | O | Q | P | L | I | V | A | G | I | I | U | A | H | Y | P | Y | L | T | Y |
| F | Y | K | W | D | K | K | C | Q | O | O | Z | R | W | K | T | S | T | O | R | D |
| C | Q | M | A | J | L | F | O | W | Y | R | B | W | D | M | G | O | E | I | D | T |
| V | L | E | Z | Q | H | V | I | I | W | S | O | Q | F | N | N | M | D | K | Q | P |
| H | A | W | M | S | Q | L | Y | O | I | M | Y | A | K | F | W | I | F | U | J | I |
| Y | Q | T | L | A | W | O | H | P | R | Q | W | S | O | Q | S | T | N | W | N | O |
| R | U | Y | O | X | S | E | E | L | I | W | X | D | P | A | A | P | O | E | D | U |
| F | I | P | P | C | A | W | S | S | P | S | Z | X | T | S | I | O | Y | X | W | T |
| M | K | Q | I | H | D | C | O | A | W | Z | W | Z | U | P | O | U | W | N | P | G |
| K | L | Z | Y | U | X | F | K | Z | S | S | V | J | G | K | P | R | K | M | K | H |
| I | G | S | U | W | G | I | M | X | Z | E | S | L | C | G | E | F | J | Q | Z | V |
| U | F | A | R | Q | H | U | K | B | D | U | L | P | F | L | W | T | H | R | X | B |
There are no repeats in the number list in the clue, so I printed out the text file and sliced it up by numbered column. I rearranged the slices to the order of the numbers in the clue. Reading the letters in a diagonal from the top left to the bottom right, in that order, provides the phrase: WELL I AM GLAD THAT IS OVER and the flag is formatted as: flag{WELLIAMGLADTHATISOVER}
TeachThemToHack (Recon)
In 2018 NeverlanCTF was one of the Keynotes for a security conference. There is a video of it on youtube. I remember seeing a flag. This one is not as easy as you think.
A bit of Googling found the presentation title Teach Them To Hack and that turned up in the 2018 keynotes for SaintCon. The video is available on YouTube at: https://www.youtube.com/watch?v=1wthauUWsGI
Scrubbing through the video found the NeverlanCTF keynote about 1h45m in, and at 1:49:40, there is an example of a CTF flag: flag{N3v3r_g0nna_g1v3_y0u_up}
Binary 3 (Binary)
Another day, another disgruntled engineer. It seems that the login is working fine, but some portions of the application are broken. Do you think you could fix the the code and retrieve the flag?
This included a get_flag.dms file. Looking at the file in a hex editor, it is an ELF binary (a Linux executable). There is some plain text about a username and password and the URL www.gr3yR0n1n.com . This site is just a grey background with the words “The Ashen Coloured Wanderer” in white.
Running it through strings (strings get_flag.dms) in Kali, also brings up admin near username (perhaps username: admin password: www.gr3yR0n1n.com?). Looking back into the hex editor, there is a series of separated characters following admin with = padding at the end. a2 Vl cC Bs b2 9r aW 5n LC Bu b3 Qg dG hl IG Zs YW c=
But it just decodes to “keep looking, not the flag”
Executing the file (./getflag.dms), prompts for a username and password. The admin username is accepted, but the greyronin password is “incorrect”.
Opened it in IDA – there are functions(?) f, l, a, and g. I can see the username and password, but don’t know why the password isn’t working.
Bash 1 (BashNinjas Bash Games)
ssh -p 3333 neverlan@157.230.73.80
password:neverlan
Opening a terminal and connecting to the remote server using the provided ssh command and password, starts the Son of Honor game at level:neverlan. The instructions are “ For this challenge you need to get the contents of Welcome.txt. At the command line, the ls command shows only one file in the current directory – Welcome.txt. Opening that file (cat Welcome.txt), reveals the level1 password “act-with-honor-and-honor-will-aid-you”. Formatted it gives: flag{act-with-honor-and-honor-will-aid-you}
Bash 2 (BashNinjas Bash Games)
ssh -p 3333 level1@157.230.73.80
Use Bash 1 password
Connecting to level1 using the password from Bash 1, we get level:level1 with the instructions “We’re going to play hide and seek. I’ll hide a file and you seek for it.”
Looking at the current directory with ls gives no results, but ‘ls -al’ shows hidden files, including .honor-code.txt, which includes the level2 password. Formatted as a flag, we get: flag{the-only-path-to-honor-is-to-stick-to-your-chosen-code}.
A little additional poking around in the file structure shows that all of the levels have their own folder in home directory, but permissions do not allow their files to be read.
Bash 3 (BashNinjas Bash Games)
ssh -p 3333 level2@157.230.73.80
Use Bash 2 password
Since we’re just using different users and finding their passwords, I stayed in the session and switched users to level2 using the Bash 2 password. Now the instructions are “OK. So you found the hidden file. How about trying to find the password in plain sight? You have to figure out how to sift through the much though…”
The folder contains the canyoufindme.txt file, which is full of lines of text. Piping to grep to look for the level3 password (cat canyoufindme.txt | grep level) reveals the level3 password for the flag: flag{child-of-honor}
Bash 4 (BashNinjas Bash Games)
ssh -p 3333 level3@157.230.73.80
Use Bash 3 password
Switching users to level3 using the Bash 3 password, we get the instructions “So you know how to use grep or some other similar program. Good for you. Now can you do the same with a binary file?”. The “random” file in this directory contains many lines of unreadable characters.
This is the first time I've grep'd in a binary file, but Google tells me it can force the file to be treated as text using the -a option (cat canyoufindme.txt | grep -a level). This reveals the level4 password for the flag: flag{only*hack^things%you$own}
Bash 5 (BashNinjas Bash Games)
ssh -p 3333 level4@157.230.73.80
Use Bash 4 password
Switching users to level4 using the Bash 4 password, we get the instructions “Nice job on that last level. I’ll have to step it up. Alright here is a file, but I won’t tell you what it is. You’ll have to figure that out on your own.” There is a file called nextlevel in this folder.
Using the file command (file nextlevel), we can see that it is a gzip file which compresses a principles.txt file. Unzipping the file using gunzip (gunzip nextlevel) gives an error about an unknown suffix. Renaming the file to nextlevel.gz (mv nextlevel nextlevel.gz) lets us run the gunzip again, but successfully this time. The contents of the resulting unzipped nextlevel file contain the level5 password for a flag: flag{on-my-honor-i-will-do-my-best}
Bash 6 (BashNinjas Bash Games)
ssh -p 3333 level5@157.230.73.80
Use Bash 5 password
Switching users to level5 using the Bash 5 password, we get the instructions “Look around for more guidance.” This folder contains a Syl.jpg file and values.txt file. The values.txt file contains a further clue that “you probably want to pull the image file to your computer and look at it” and advice that Googling “Transfer files over SSH“ would be helpful.
Copying the file to my computer from my machine:
scp -P 3333 level5@157.230.73.80:/home/level5/Syl.jpg ./Downloads/
I am able to open the JPG containing the level6 password for the flag: flag{have-you-memorized-the-code-yet}
Bash 7 (BashNinjas Bash Games)
ssh -p 3333 level6@157.230.73.80
Use Bash 6 password
Switching users to level6 using the Bash 6 password, we get the instructions “Look in level7.txt. You’ll have to figure out what to do with that on your own.” The level7.txt contains a string of characters ending with =, so copying and pasting into a Base64 decoder reveals the level7 password for the flag: flag{white-hats-have-values-and-rules}
Bash 8 (BashNinjas Bash Games)
ssh -p 3333 level7@157.230.73.80
Use Bash 7 password
Switching users to level7 using the Bash 7 password, we get the instructions “This is almost the same thing as the last level, just gotta do one more step.” The level8.txt file contains more similarly encoded text but without the (non-mandatory) = at the end. Decoding from Base64 gives unreadable text. There are / repeatedly that seem to indicate line breaks.
File indicates that it is ASCII text, and search using the first few characters provides an example of gzip’d files that look similar and share the H4sIA start. So, the first step is to decode the Base64 text into a new file (base64 -d level8.txt > level8.gz), then gunzip’ing that file to reveal the level8 password and flag: flag{my-wit-ran-out-5-levels-ago}
Update – 21 Apr 2019: So, out of the blue the other day, I got an interesting email:
Dear Drew,
I was searching in internet to find some clues about H4sIA string. Your blog came up where you explained about this string. Actually I have a Ascii text which I need to analyse. The Ascii code is in the attachment. I did the step you mentioned
base64 -D ~/Downloads/l8.txt > ~/Downloads/l8.gz
I opened the 18.gz file but in this point I need your help to find out what is inside?Is it password or something?
So, I popped open a VM, cut it off from my host system, and downloaded it for a look.
The Ascii.txt file contained that same H4sIA header string, but didn’t give up the goods as soon as it was base64 decoded into a gzip file like I had done in the NeverLAN challenge. That process produces an “invalid input” error and the resulting file is incomplete. In order to fix that, we need to also use the -i option for the base64 command, which will ignore any non-alphabetic characters (e.g. line separators) when decoding. Checking the file type of the resulting file, we get a POSIX tar archive, rather than a gzip, containing a file called data. Renaming the file with the .tar suffix and unarchiving that file (tar -xf file.tar), we get another ASCII text file. The contents of this file are also base64 encoded, although they didn’t contain any problematic characters. In the resulting file, I can see an email address for a managed detection and response company, and file tells us it’s a PGP public key.
My interest was piqued, so I checked back with the sender, and they replied:
Actually this was a question, I got asked during a job interview so the source of is unkown for me. As job interview was for malware analyst, It seems athis could be, file sent by malware.
So, if it looks like these CTF challenges are just for fun, think again. These are practical challenges (admittedly some more than others) of the sort that appear on the job and in interviews.
Back to the Ninja Bashing...
Bash 9 (BashNinjas Bash Games)
ssh -p 3333 level8@157.230.73.80
Use Bash 8 password
Switching users to level8 using the Bash 8 password, we get the instructions “Your goal here is to decrypt ‘level9.enc’. There’s a clue around here somewhere.” The folder contains the level9.enc and the hidden .clue file.
The clue says “aes-256-cbc encryption password: level9please” and the level9.enc contains a short string: U2FsdGVkX1/RjLebmJbThsz7hNuLEJnRevchxfV4RTonlVjXvbUHFMHnitt/TJSt
Trying the openssl decoder (openssl enc -aes-256-cbc -d -in level9.enc -out file.txt) and providing the encryption password gives a “bad magic number” error. The string looks like Base64, so I decoded it to a test file and used openssl on that file, revealing the level9 password and flag: flag{please-someone-help}
Bash 10 (BashNinjas Bash Games)
ssh -p 3333 level9@157.230.73.80
Use Bash 9 password
Switching users to level9 using the Bash 9 password, we get the instructions “Congrats. You win. Almost…You’ve just got to get the flag in final.txt. You didn’t say the magic word. Goodbye” and it does not log into level9. Indeed, trying to ssh directly in as the level9 user gets you disconnected, so it’s good that I was just switching users.
Moving to the level9 directory, I can see the final.txt file, but do not have permissions to read it as the files in level9 are rw for owner only and owned by level9. The sudo command is not installed.
The password seems to be correct, but the issue appears to be with the startup script for the level9 user, which I also cannot alter due to permissions. An attempt to scp the file out over ssh confirms it with the error “/home/level9/.bashrc: line 4: logout: not login shell: use `exit'”.
So, a little Googling later, I found a way to skip the startup script:
ssh -p 3333 level9@157.230.73.80 "bash --noprofile --norc"
It produces the same message as above, but leaves an open shell where the final.txt file can be read. The flag is: flag{i-am-now-a-child-of-honor}
Das Blog (Web)
Word on the street, Johnny's got a blog. Seems he doesn't know how to escape his inputs.
https://challenges.neverlanctf.com:1125
Browsing to the site, its URL is appended with login.php? and there are two text fields for Username and Password and a Login button. Most test entries (e.g. admin, admin) result in the message “Sorry, That Username / Password” is incorrect”. Beginning a username with ‘, however, results in the message “There was a problem when looking for user. Please try again.”
This took quite a bit of Googling, as most of the pages out there are focussed on preventing this vulnerability. Eventually, I came across an entry on https://www.exploit-db.com/exploits/6991that included the following:
Username: ' or 1=1# Password: no-deface;
This returned the result "You are now logged in as Johnny with permissions admin" and a link to the main page, where we find the flag: flag{3sc4pe_Y0ur_1npu7s}
Das Blog 2 (Web)
Well, we really showed Johnny. It looks like he made some changes... But he still isn't escaping his inputs. Teach him a lesson.
https://challenges.neverlanctf.com:1130
The setup is the same as Das Blog, and I immediately tried the exploit from Das Blog. That got me “logged in as Johnny with permissions user” and a link to the main page.
The main page shows I have DEFAULT permissions, and no flag is visible, but there is a hint “I can set posts to only show for users with special permissions!“
The # working in the previous exploit indicates that we are attacking a MySQL database. I tried variations to get admin access, but without success.
e,g,
' or 1=1 'and permissions='admin'#
Johnny' or 1=1#
Johnny'and permissions='admin'
' and permission=’admin’ or 1=1#
PW1-16 (Password Cracking)
Oh no. We did it. We're releasing password cracking challenges on the last day of the CTF. WHAT ARE YOU GOING TO DO!?!? You don't have a ton of time to brute force these.
This is our little way of saving the planet by saving your graphics cards from sucking all its' energy.
Enjoy!
Hash:$1$78V0y281$b0f95SAqd2BGFM0R94rIQ/
Note: These challenges aren't in any order of difficulty or anything. They're just here.
The $1$ indicates that this is an MD5 hash, and so are all of the 15 PW challenges. I copied them into a file in Kali and set John the Ripper on them in brute force mode (john –incremental hashes.txt).
I didn’t get any cracked before the CTF finished – they were only released in the last hour or so, and my Kali VM doesn’t have a dedicated GPU to speed things up.
It took a day or so, but eventually I got two hashes (n30 and pwned), but the site had shutdown before I could check them. At that point I just shut down John, since there were no confirmations and no points.
React To This (Web)
It looks like someone set up their react site wrong...
https://challenges.neverlanctf.com:1145
A look at the web Inspector for this very simple page shows the expected HTML code, a javascript script call, and a comment that “You need to enable Javascript to view this website”. Looking in the Inspector’s Debugger, I found an Admin.js page that contained the variable flg = s3cur3_y0ur_s3ss10ns and some formatting script “f{'l'}a{'g'}{'{'+flg+'}'}”, which combine to form the flag: flag{s3cur3_y0ur_s3ss10ns}
Console (Web)
You control the browser
https://challenges.neverlanctf.com:1120
The page has a single text field and a submit button. Looking in the web Inspector, there is a script that is checking the input against an md5 hash. The code that checks the hashed input against a reference hash triggers a switch getThat(‘Y’) if they match and getThat(‘N’) if they don’t. Switching to the Console in the Inspector, I entered getThat(‘Y’) and the flag was revealed: flag{console_controls_js}
Dirty Validate (Web)
To keep my server from doing a lot of work, I made javascript do the heavy lifting of checking a user's password
https://challenges.neverlanctf.com:1135
The page includes Username and Password fields, and there is a length javascript script at the end of the page when viewed in the web Inspector.
I didn’t get this one, but was around when a teammate did. Somehow they got a list of users, and noticed that the password validation down in the javascript was the name again but URI encoded (so, spaces encoded as %20).
SQL Trivia 1 (Trivia)
The oldest SQL Injection Vulnerability. The flag is the vulnerability ID.
flag{CVE-2000-1233}
SQL Trivia 2 (Trivia)
In MSSQL Injection Whats the query to see what version it is?
flag{@@VERSION}
Sea Quail (Trivia)
A domain-specific language used in programming and designed for managing data held in a relational database management system, or for stream processing in a relational data stream management system.
flag{SQL}
64 Characters (Trivia)
A group of similar binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation.
flag{Base64}
With Some Milk (Trivia)
A small piece of data sent from a website and stored on the user's computer by the user's web browser while the user is browsing.
flag{Cookie}
Beep Boop (Trivia)
A standard used by websites to communicate with web crawlers and other web robots. The standard specifies how to inform the web robot about which areas of the website should not be processed or scanned
flag{Robots.txt}
Alright…who is this? (Trivia)
A command line tool that tells you whois hosting a particular website.
flag{whois}
So many policies… (Trivia)
What are the policies called that you use to grant access to your AWS S3 buckets and objects to the general public?
flag{accesscontrollists}
Bucket Name = Domain Name (Trivia)
Here's some info for future challenges. Fill in the blank.
When hosting a site as an S3 bucket, the bucket name must ____ the domain name.
flag{Equal}
All around the globe! (Trivia)
What type of namespace prevents two AWS S3 buckets having the same name?
flag{global}
AWShoot (Trivia)
What does AWS stand for?
flag{AmazonWebServices}
C’mere piggy (Trivia)
Why make bacon when you can make a cipher instead?
If only I could remember what it's called...
flag{pigpen}
Sorry…you don’t have the privileges for this! (Trivia)
What does sudo stand for?
flag{superuserdo}
Let’s get on the right PATH (Trivia)
What is $PATH on linux?
Don't think too hard on this one :)
flag{/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:}
Bash all the things p1 (Trivia)
When bash is invoked as an interactive login shell it first reads and executes commands from this file.
flag{.bash_profile}
Bash all the things p2 (Trivia)
When bash is invoked as an interactive non-login shell it first reads and executes commands from this file
flag{.bashrc}
FINAL RESULTS
Team: 4145 points
Final Rank: 118 out of 1091
Me: 3320 points
Final Rank: 151 out of 3133